palo alto networks pcdra practice test
palo alto networks certified detection and remediation analyst
Question 1
Which of the following is NOT a precanned script provided by Palo Alto Networks?
- A. delete_file
- B. quarantine_file
- C. process_kill_name
- D. list_directories
Answer:
b
Question 2
If you have an isolated network that is prevented from connecting to the Cortex Data Lake, which type of Broker VM setup can you use to facilitate the communication?
- A. Broker VM Pathfinder
- B. Local Agent Proxy
- C. Local agent installer
- D. Broker VM Syslog Collector
Answer:
b
Question 3
When creating a custom XQL query in a dashboard, how would a user save that XQL query to the Widget Library?
- A. Click the three dots on the widget and then choose Save and this will link the query to the Widget Library.
- B. This isnt supported, you have to exit the dashboard and go into the Widget Library first to create it.
- C. Click on Save to Action Center in the dashboard and you will be prompted to give the query a name and description.
- D. Click on Save to Widget Library in the dashboard and you will be prompted to give the query a name and description.
Answer:
d
Question 4
After scan, how does file quarantine function work on an endpoint?
- A. Quarantine takes ownership of the files and folders and prevents execution through access control.
- B. Quarantine disables the network adapters and locks down access preventing any communications with the endpoint.
- C. Quarantine removes a specific file from its location on a local or removable drive to a protected folder and prevents it from being executed.
- D. Quarantine prevents an endpoint from communicating with anything besides the listed exceptions in the agent profile and Cortex XDR.
Answer:
c
Question 5
As a Malware Analyst working with Cortex XDR you notice an alert suggesting that there was a prevented attempt to open a malicious Word document. You learn from the WildFire report and AutoFocus that this document is known to have been used in Phishing campaigns since 2018. What steps can you take to ensure that the same document is not opened by other users in your organization protected by the Cortex XDR agent?
- A. Enable DLL Protection on all endpoints but there might be some false positives.
- B. Create Behavioral Threat Protection (BTP) rules to recognize and prevent the activity.
- C. No step is required because Cortex shares IOCs with our fellow Cyber Threat Alliance members.
- D. No step is required because the malicious document is already stopped.
Answer:
b
Question 6
Which of the following represents the correct relation of alerts to incidents?
- A. Only alerts with the same host are grouped together into one Incident in a given time frame.
- B. Alerts that occur within a three hour time frame are grouped together into one Incident.
- C. Alerts with same causality chains that occur within a given time frame are grouped together into an Incident.
- D. Every alert creates a new Incident.
Answer:
a
Question 7
Which Exploit Protection Module (EPM) can be used to prevent attacks based on OS function?
- A. Memory Limit Heap Spray Check
- B. DLL Security
- C. UASLR
- D. JIT Mitigation
Answer:
b
Question 8
Where can SHA256 hash values be used in Cortex XDR Malware Protection Profiles?
- A. in the macOS Malware Protection Profile to indicate allowed signers
- B. in the Linux Malware Protection Profile to indicate allowed Java libraries
- C. SHA256 hashes cannot be used in Cortex XDR Malware Protection Profiles
- D. in the Windows Malware Protection Profile to indicate allowed executables
Answer:
d
Question 9
Which Type of IOC can you define in Cortex XDR?
- A. destination port
- B. e-mail address
- C. full path
- D. App-ID
Answer:
c
Question 10
Which statement is true based on the following Agent Auto Upgrade widget?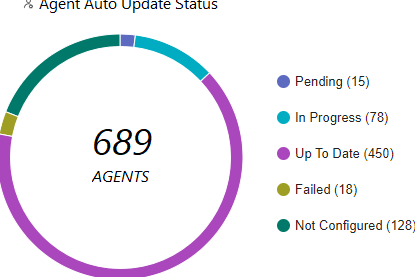
- A. There are a total of 689 Up To Date agents.
- B. Agent Auto Upgrade was enabled but not on all endpoints.
- C. Agent Auto Upgrade has not been enabled.
- D. There are more agents in Pending status than In Progress status.
Answer:
b