microsoft sc-100 practice test
Microsoft Cybersecurity Architect
Question 1
HOTSPOT Your company has an Azure App Service plan that is used to deploy containerized web apps.
You are designing a secure DevOps strategy for deploying the web apps to the App Service plan.
You need to recommend a strategy to integrate code scanning tools into a secure software development lifecycle. The code must be scanned during the following two phases:
Uploading the code to repositories
Building containers
Where should you integrate code scanning for each phase? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area: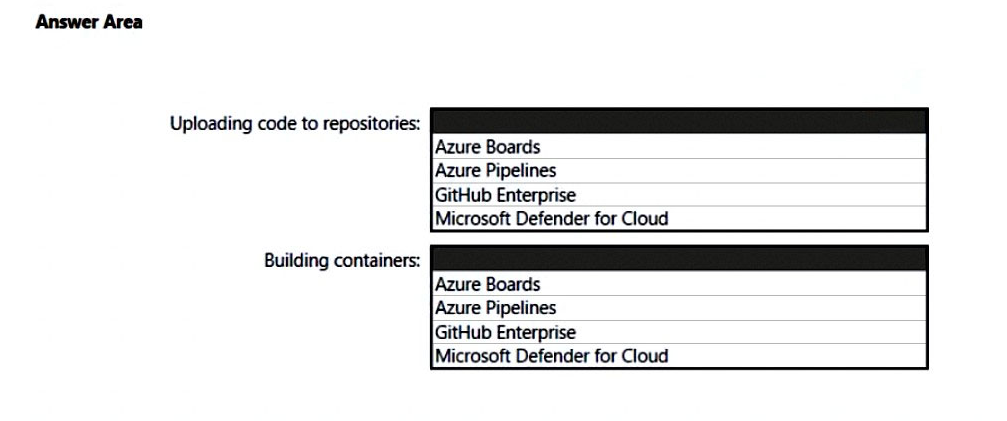
Answer:
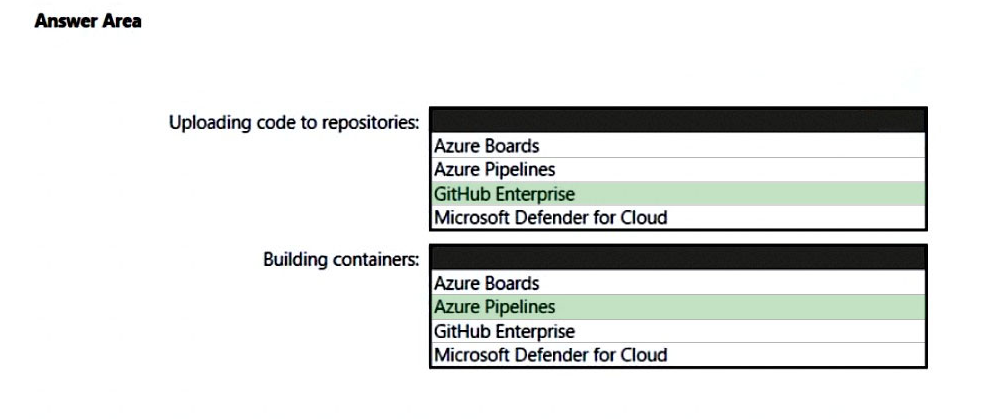
Box 1: GitHub Enterprise -
A GitHub Advanced Security license provides the following additional features:
Code scanning - Search for potential security vulnerabilities and coding errors in your code.
Secret scanning - Detect secrets, for example keys and tokens, that have been checked into the repository. If push protection is enabled, also detects secrets when they are pushed to your repository.
Etc.
Code scanning is a feature that you use to analyze the code in a GitHub repository to find security vulnerabilities and coding errors. Any problems identified by the analysis are shown in GitHub Enterprise Cloud.
Box 2: Azure Pipelines -
Building Containers with Azure DevOps using DevTest Pattern with Azure Pipelines
The pattern enabled as to build container for development, testing and releasing the container for further reuse (production ready).
Azure Pipelines integrates metadata tracing into your container images, including commit hashes and issue numbers from Azure Boards, so that you can inspect your applications with confidence.
Incorrect:
* Not Azure Boards: Azure Boards provides software development teams with the interactive and customizable tools they need to manage their software projects.
It provides a rich set of capabilities including native support for Agile, Scrum, and Kanban processes, calendar views, configurable dashboards, and integrated reporting.
* Not Microsoft Defender for Cloud
Microsoft Defender for Containers is the cloud-native solution that is used to secure your containers so you can improve, monitor, and maintain the security of your clusters, containers, and their applications.
You cannot use Microsoft Defender for Cloud to scan code, it scans images.
Reference:
https://docs.github.com/en/enterprise-cloud@latest/get-started/learning-about-github/about-github-advanced-security https://microsoft.github.io/code-with-engineering-playbook/automated-testing/tech-specific-samples/azdo-container-dev-test-release/
Question 2
Your company is preparing for cloud adoption.
You are designing security for Azure landing zones.
Which two preventative controls can you implement to increase the secure score? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
- A. Azure Web Application Firewall (WAF)
- B. Azure Active Directory (Azure AD) Privileged Identity Management (PIM)
- C. Microsoft Sentinel
- D. Azure Firewall
- E. Microsoft Defender for Cloud alerts
Answer:
bc
B: Azure identity and access for landing zones, Privileged Identity Management (PIM)
Use Azure AD Privileged Identity Management (PIM) to establish zero-trust and least privilege access. Map your organization's roles to the minimum access levels needed. Azure AD PIM can use Azure native tools, extend current tools and processes, or use both current and native tools as needed.
Azure identity and access for landing zones, Design recommendations include:
* (B) Use Azure AD managed identities for Azure resources to avoid credential-based authentication. Many security breaches of public cloud resources originate with credential theft embedded in code or other text. Enforcing managed identities for programmatic access greatly reduces the risk of credential theft.
* Etc.
C: Improve landing zone security, onboard Microsoft Sentinel
You can enable Microsoft Sentinel, and then set up data connectors to monitor and protect your environment. After you connect your data sources using data connectors, you choose from a gallery of expertly created workbooks that surface insights based on your data. These workbooks can be easily customized to your needs.
Note: Landing zone security best practices
The following list of reference architectures and best practices provides examples of ways to improve landing zone security:
Microsoft Defender for Cloud: Onboard a subscription to Defender for Cloud.
Microsoft Sentinel: Onboard to Microsoft Sentinel to provide a security information event management (SIEM) and security orchestration automated response
(SOAR) solution.
Secure network architecture: Reference architecture for implementing a perimeter network and secure network architecture.
Identity management and access control: Series of best practices for implementing identity and access to secure a landing zone in Azure.
Network security practices: Provides additional best practices for securing the network.
Operational security provides best practices for increasing operational security in Azure.
The Security Baseline discipline: Example of developing a governance-driven security baseline to enforce security requirements.
Incorrect:
Not E: Implementing alerts is not a preventive measure.
Reference:
https://docs.microsoft.com/en-us/azure/cloud-adoption-framework/ready/landing-zone/design-area/identity-access-landing-zones https://docs.microsoft.com/en-us/azure/sentinel/quickstart-onboard
Question 3
You use Azure Pipelines with Azure Repos to implement continuous integration and continuous deployment (CI/CD) workflows for the deployment of applications to Azure.
You need to recommend what to include in dynamic application security testing (DAST) based on the principles of the Microsoft Cloud Adoption Framework for Azure.
What should you recommend?
- A. unit testing
- B. penetration testing
- C. dependency checks
- D. threat modeling
Answer:
b
Question 4
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have an Azure subscription that has Microsoft Defender for Cloud enabled.
You are evaluating the Azure Security Benchmark V3 report.
In the Secure management ports controls, you discover that you have 0 out of a potential 8 points.
You need to recommend configurations to increase the score of the Secure management ports controls.
Solution: You recommend enabling the VMAccess extension on all virtual machines.
Does this meet the goal?
- A. Yes
- B. No
Answer:
b
Instead: You recommend enabling just-in-time (JIT) VM access on all virtual machines.
Note:
Secure management ports - Brute force attacks often target management ports. Use these recommendations to reduce your exposure with tools like just-in-time
VM access and network security groups.
Recommendations:
- Internet-facing virtual machines should be protected with network security groups
- Management ports of virtual machines should be protected with just-in-time network access control
- Management ports should be closed on your virtual machines
Reference:
https://docs.microsoft.com/en-us/azure/defender-for-cloud/secure-score-security-controls
Question 5
HOTSPOT You need to recommend a strategy for App Service web app connectivity. The solution must meet the landing zone requirements.
What should you recommend? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area: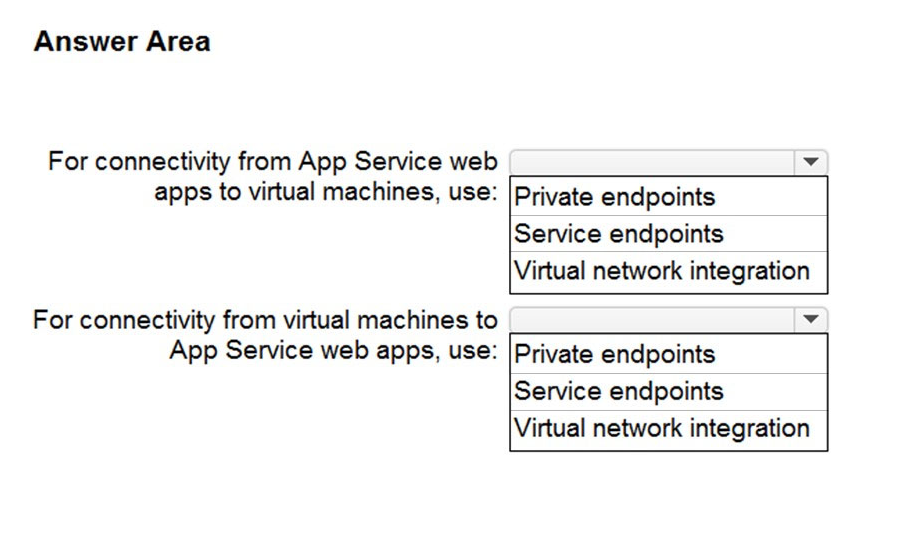
Answer:
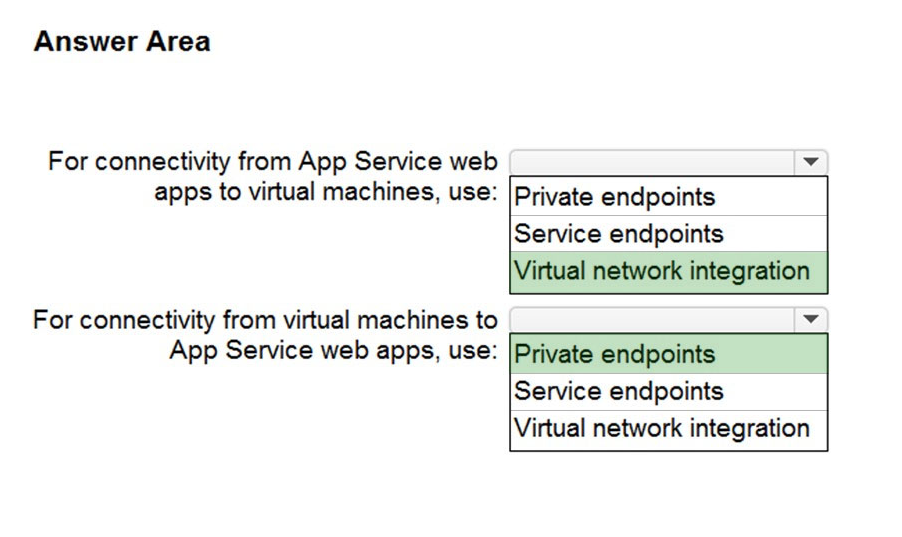
Box 1: Virtual network integration
Integrate your app with an Azure virtual network.
With Azure virtual networks, you can place many of your Azure resources in a non-internet-routable network. The App Service virtual network integration feature enables your apps to access resources in or through a virtual network.
Box 2: Private endpoints -
Ensure that the Azure virtual machines in each landing zone communicate with Azure App Service web apps in the same zone over the Microsoft backbone network, rather than over public endpoints.
A virtual machine can connect to the web app across the private endpoint.
Reference:
https://docs.microsoft.com/en-us/azure/app-service/overview-vnet-integration https://docs.microsoft.com/en-us/azure/private-link/tutorial-private-endpoint-webapp-portal
Question 6
Your company has an Azure subscription that has enhanced security enabled for Microsoft Defender for Cloud.
The company signs a contract with the United States government.
You need to review the current subscription for NIST 800-53 compliance.
What should you do first?
- A. From Defender for Cloud, enable Defender for Cloud plans.
- B. From Azure Policy, assign a built-in initiative that has a scope of the subscription.
- C. From Microsoft Defender for Cloud Apps, create an access policy for cloud applications.
- D. From Azure Policy, assign a built-in policy definition that has a scope of the subscription.
Answer:
b
Question 7
You are designing a new Azure environment based on the security best practices of the Microsoft Cloud Adoption Framework for Azure. The environment will contain one subscription for shared infrastructure components and three separate subscriptions for applications.
You need to recommend a deployment solution that includes network security groups (NSGs), Azure Firewall, Azure Key Vault, and Azure Bastion. The solution must minimize deployment effort and follow security best practices of the Microsoft Cloud Adoption Framework for Azure.
What should you include in the recommendation?
- A. the Azure landing zone accelerator
- B. the Azure Well-Architected Framework
- C. Azure Security Benchmark v3
- D. Azure Advisor
Answer:
a
Question 8
Your company plans to apply the Zero Trust Rapid Modernization Plan (RaMP) to its IT environment.
You need to recommend the top three modernization areas to prioritize as part of the plan.
Which three areas should you recommend based on RaMP? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
- A. data, compliance, and governance
- B. infrastructure and development
- C. user access and productivity
- D. operational technology (OT) and IoT
- E. modern security operations
Answer:
ace
Question 9
Your company has an Azure subscription that uses Microsoft Defender for Cloud.
The company signs a contract with the United States government.
You need to review the current subscription for NIST 800-53 compliance.
What should you do first?
- A. From Defender for Cloud, enable Defender for Cloud plans.
- B. From Defender for Cloud, review the Azure security baseline for audit report.
- C. From Defender for Cloud, add a regulatory compliance standard.
- D. From Microsoft Defender for Cloud Apps, create an access policy for cloud applications.
Answer:
c
Question 10
Your company is moving a big data solution to Azure.
The company plans to use the following storage workloads:
Azure Storage blob containers
Azure Data Lake Storage Gen2
Azure Storage file shares
Azure Disk Storage
Which two storage workloads support authentication by using Azure Active Directory (Azure AD)? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
- A. Azure Storage file shares
- B. Azure Disk Storage
- C. Azure Storage blob containers
- D. Azure Data Lake Storage Gen2
Answer:
cd
C: Azure Storage supports using Azure Active Directory (Azure AD) to authorize requests to blob data. With Azure AD, you can use Azure role-based access control (Azure RBAC) to grant permissions to a security principal, which may be a user, group, or application service principal. The security principal is authenticated by Azure AD to return an OAuth 2.0 token. The token can then be used to authorize a request against the Blob service.
You can scope access to Azure blob resources at the following levels, beginning with the narrowest scope:
* An individual container. At this scope, a role assignment applies to all of the blobs in the container, as well as container properties and metadata.
* The storage account.
* The resource group.
* The subscription.
* A management group.
D: You can securely access data in an Azure Data Lake Storage Gen2 (ADLS Gen2) account using OAuth 2.0 with an Azure Active Directory (Azure AD) application service principal for authentication. Using a service principal for authentication provides two options for accessing data in your storage account:
A mount point to a specific file or path
Direct access to data -
Incorrect:
Not A: To enable AD DS authentication over SMB for Azure file shares, you need to register your storage account with AD DS and then set the required domain properties on the storage account. To register your storage account with AD DS, create an account representing it in your AD DS.
Reference:
https://docs.microsoft.com/en-us/azure/storage/blobs/authorize-access-azure-active-directory https://docs.microsoft.com/en-us/azure/databricks/data/data-sources/azure/adls-gen2/azure-datalake-gen2-sp-access