Juniper jn0-635 practice test
Security, Professional Exam
Question 1
You are asked to look at a configuration that is designed to take all traffic with a specific source ip
address and forward the
traffic to a traffic analysis server for further evaluation. The configuration is no longer working as
intended.
Referring to the exhibit which change must be made to correct the configuration?
- A. Apply the filter as in input filter on interface xe-0/2/1.0
- B. Apply the filter as in input filter on interface xe-0/0/1.0
- C. Create a routing instance named default
- D. Apply the filter as in output filter on interface xe-0/1/0.0
Answer:
B
Question 2
Exhibit.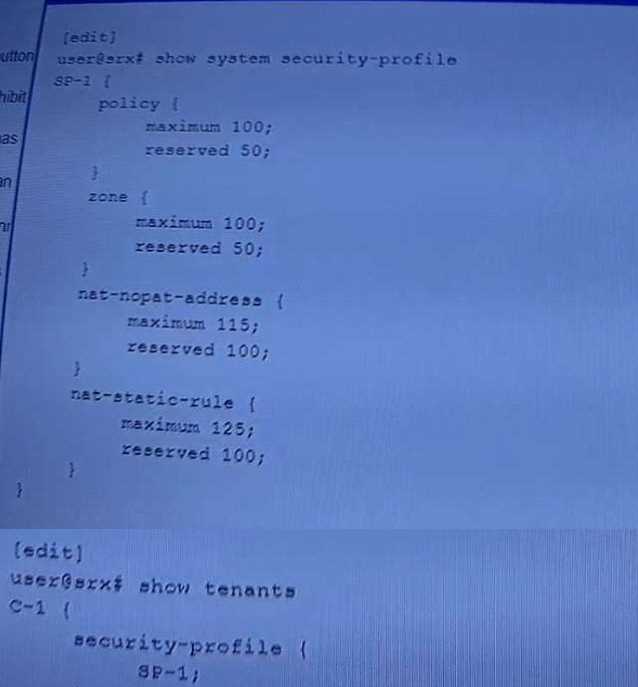
Referring to the exhibit, which two statements are true? (Choose two.)
- A. The c-1 TSYS has a reservation for the security flow resource.
- B. The c-1 TSYS can use security flow resources up to the system maximum.
- C. The c-1 TSYS cannot use any security flow resources.
- D. The c-1 TSYS has no reservation for the security flow resource.
Answer:
C, D
Explanation:
https://www.juniper.net/documentation/en_US/junos/topics/topic-map/security-profile-logical-system.html
Question 3
What are two important function of the Juniper Networks ATP appliance solution? (Choose two.).
- A. Statistics
- B. Analysis
- C. Detection
- D. Filtration
Answer:
B, C
Explanation:
https://www.juniper.net/us/en/products-services/security/advanced-threat-prevention/
Question 4
Which three type of peer devices are supported for Cos-Based IPsec VPN?
- A. High-end SRX Series device
- B. cSRX
- C. vSRX
- D. Branch-end SRX Series devics
Answer:
A, C, D
Question 5
You have the NAT rule, shown in the exhibit, applied to allow communication across an IPsec tunnel
between your two sites with identical networks. Which statement is correct in this scenario?
- A. The NAT rule with translate the source and destination addresses.
- B. The NAT rule will only translate two addresses at a time.
- C. The NAT rule in applied to the N/A routing instance.
- D. 10 packets have been processed by the NAT rule.
Answer:
A
Question 6
You are connecting two remote sites to your corporate headquarters site; you must ensure that all
traffic is secured and
only uses a single Phase 2 SA for both sites.
In this scenario, which VPN should be used?
- A. An IPsec group VPN with the corporate firewall acting as the hub device.
- B. Full mesh IPsec VPNs with tunnels between all sites.
- C. A hub-and-spoke IPsec VPN with the corporate firewall acting as the hub device.
- D. A full mesh Layer 3 VPN with the corporate firewall acting as the hub device.
Answer:
A
Explanation:
https://www.juniper.net/us/en/local/pdf/app-notes/3500202-en.pdf
Question 7
Exhibit.
Referring to the exhibit, a spoke member of an ADVPN is not functioning correctly.
Which two commands will solve this problem? (Choose two.)
- A. [edit interfaces] user@srx# delete st0.0 multipoint
- B. [edit security ike gateway advpn-gateway] user@srx# delete advpn partner
- C. [edit security ike gateway advpn-gateway] user@srx# set version v1-only
- D. [edit security ike gateway advpn-gateway] user@srx# set advpn suggester disable
Answer:
B, D
Explanation:
https://www.juniper.net/documentation/en_US/junos/topics/topic-map/security-auto-discovery-vpns.html
Question 8
You are asked to configure a security policy on the SRX Series device. After committing the policy, you
receive the Policy is out of sync between RE and PFE <SPU-name(s)>. error.
Which command would be used to solve the problem?
- A. request security polices resync
- B. request service-deployment
- C. request security polices check
- D. restart security-intelligence
Answer:
A
Explanation:
https://kb.juniper.net/InfoCenter/index?page=content&id=KB30443&cat=SRX_SERIES&actp=LIST
Question 9
Exhibit.
Referring to the exhibit, which two statements are true? (Choose two.)
- A. Juniper Networks will not investigate false positives generated by this custom feed.
- B. The custom infected hosts feed will not overwrite the Sky ATP infected host’s feed.
- C. The custom infected hosts feed will overwrite the Sky ATP infected host’s feed.
- D. Juniper Networks will investigate false positives generated by this custom feed.
Answer:
A, C
Explanation:
https://www.juniper.net/documentation/en_US/junos-space18.1/policy-enforcer/topics/task/configuration/junos-space-policyenforcer-custom-feeds-infected-host-configure.html
Question 10
You must implement an IPsec VPN on an SRX Series device using PKI certificates for authentication.
As part of the implementation, you are required to ensure that the certificate submission, renewal,
and retrieval processes are handled
automatically from the certificate authority.
In this scenario, which statement is correct.
- A. You can use CRL to accomplish this behavior.
- B. You can use SCEP to accomplish this behavior.
- C. You can use OCSP to accomplish this behavior.
- D. You can use SPKI to accomplish this behavior.
Answer:
B
Explanation:
Explanation:
Certificate
Renewal
The renewal of certificates is much the same as initial certificate enrollment except you are just
replacing
an
old
certificate
(about to expire) on the VPN device with a new certificate. As with the initial certificate request, only
manual
renewal
is
supported. SCEP can be used to re-enroll local certificates automatically before they expire. Refer to
Appendix
D
for
more
details.
Question 11
You are not able to activate the SSH honeypot on the all-in-one Juniper ATP appliance.
What would be a cause of this problem?
- A. The collector must have a minimum of two interfaces.
- B. The collector must have a minimum of three interfaces.
- C. The collector must have a minimum of five interfaces.
- D. The collector must have a minimum of four interfaces.
Answer:
D
Explanation:
https://www.juniper.net/documentation/en_US/release-independent/jatp/topics/task/configuration/jatp-traffic-collectorsetting-ssh-honeypot-detection.html
Question 12
You have a webserver and a DNS server residing in the same internal DMZ subnet. The public Static
NAT addresses for
the servers are in the same subnet as the SRX Series devices internet-facing interface. You implement
DNS doctoring to
ensure remote users can access the webserver.Which two statements are true in this scenario?
(Choose two.)
- A. The DNS doctoring ALG is not enabled by default.
- B. The Proxy ARP feature must be configured.
- C. The DNS doctoring ALG is enabled by default.
- D. The DNS CNAME record is translated.
Answer:
B, C
Question 13
The monitor traffic interface command is being used to capture the packets destined to and the from
the SRX Series device.
In this scenario, which two statements related to the feature are true? (Choose two.)
- A. This feature does not capture transit traffic.
- B. This feature captures ICMP traffic to and from the SRX Series device.
- C. This feature is supported on high-end SRX Series devices only.
- D. This feature is supported on both branch and high-end SRX Series devices.
Answer:
A, D
Explanation:
https://forums.juniper.net/t5/Ethernet-Switching/monitor-traffic-interface/td-p/462528
Question 14
You opened a support ticket with JTAC for your Juniper ATP appliance. JTAC asks you to set up access
to the device
using the reverse SSH connection.Which three setting must be configured to satisfy this request?
(Choose three.)
- A. Enable JTAC remote access
- B. Create a temporary root account.
- C. Enable a JATP support account.
- D. Create a temporary admin account.
- E. Enable remote support.
Answer:
C, D,E
Explanation:
https://kb.juniper.net/InfoCenter/index?page=content&id=TN326&cat=&actp=LIST&showDraft=false
Question 15
Exhibit.
Referring to the exhibit, which two statements are true? (Choose two.)
- A. The configured solution allows IPv6 to IPv4 translation.
- B. The configured solution allows IPv4 to IPv6 translation.
- C. The IPv6 address is invalid.
- D. External hosts cannot initiate contact.
Answer:
A, C