Fortinet nse7-zta-7-2 practice test
fortinet nse 7 - zero trust access 7.2
Question 1
An administrator has to configure LDAP authentication for ZTNA HTTPS access proxy.
Which authentication scheme can the administrator apply?
- A. Basic
- B. Form-based
- C. Digest
- D. NTLM
Answer:
a
Question 2
FortiNAC has alarm mappings configured for MDM compliance failure, and FortiClient EMS is added as an MDM connector.
When an endpoint is quarantined by FortiClient EMS, what action does FortiNAC perform?
- A. The host is isolated in the registration VLAN.
- B. The host is marked at risk.
- C. The host is forced to authenticate again.
- D. The host is disabled.
Answer:
b
Question 3
Which two types of configuration can you associate with a user/host profile on FortiNAC? (Choose two.)
- A. Service Connectors
- B. Network Access
- C. Inventory
- D. Endpoint compliance
Answer:
bd
Question 4
An administrator wants to prevent direct host-to-host communication at layer 2 and use only FortiGate to inspect all the VLAN traffic.
What three things must the administrator configure on FortiGate to allow traffic between the hosts? (Choose three.)
- A. Block intra-VLAN traffic in the VLAN interface settings.
- B. Add the VLAN interface to a software switch.
- C. Configure static routes to allow subnets.
- D. Configure a firewall policy to allow the desired traffic between hosts.
- E. Configure proxy ARP to allow traffic.
Answer:
abd
Question 5
With the increase in IoT devices, which two challenges do enterprises face? (Choose two.)
- A. Bandwidth consumption due to added overhead of IoT
- B. Maintaining a high performance network
- C. Unpatched vulnerabilities in IoT devices
- D. Achieving full network visibility
Answer:
cd
Question 6
Which three statements are true about a persistent agent? (Choose three.)
- A. Supports advanced custom scans and software inventory.
- B. Can apply supplicant configuration to a host.
- C. Deployed by a login/logout script and is not installed on the endpoint.
- D. Can be used for automatic registration and authentication.
- E. Agent is downloaded and run from captive portal.
Answer:
abd
Question 7
Which three statements are true about zero-trust telemetry compliance? (Choose three.)
- A. FortiClient checks the endpoint using the ZTNA tags provided by FortiClient EMS.
- B. ZTNA tags are configured in FortiClient, based on criteria such as certificates and the logged in domain.
- C. FortiOS provides network access to the endpoint, based on the zero-trust tagging rules.
- D. FortiClient EMS sends the endpoint information received through FortiClient Telemetry to FortiOS.
- E. FortiClient EMS creates dynamic policies using ZTNA tags.
Answer:
acd
Question 8
In which FortiNAC configuration stage do you define endpoint compliance?
- A. Device onboarding
- B. Management configuration
- C. Policy configuration
- D. Network modeling
Answer:
c
Question 9
Which method is used to install passive agent on an endpoint?
- A. Deployed by using a login/logout script
- B. Agent is downloaded from Playstore
- C. Agent is downloaded and run from captive portal
- D. Installed by user or deployment tools
Answer:
a
Question 10
Refer to the exhibit.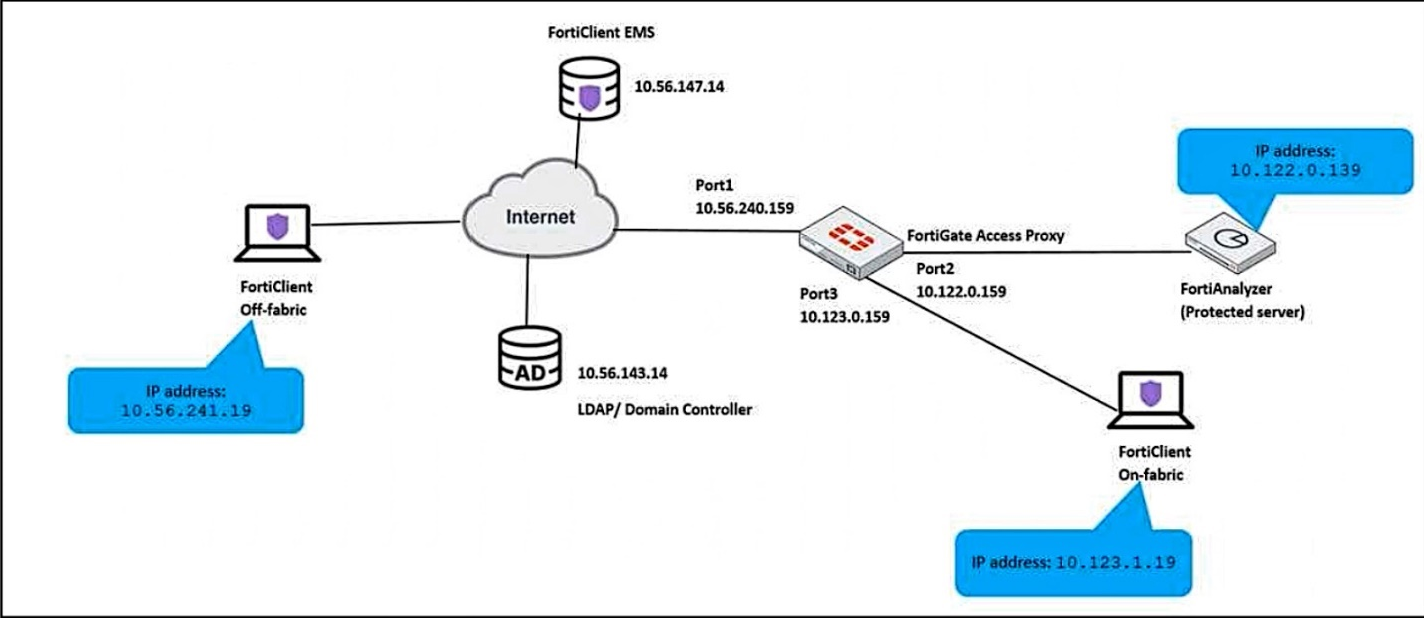
An administrator has to provide on-fabric clients with access to FortiAnalyzer using ZTNA tags.
Which two conditions must be met to achieve this task? (Choose two.)
- A. The on-fabric client should have FortiGate as its default gateway.
- B. The ZTNA server must be configured on FortiGate.
- C. The ZTNA rule must be configured on FortiClient.
- D. The IP/MAC based firewall policy must be configured on FortiGate.
Answer:
bc