comptia pt0-002 practice test
CompTIA PenTest+ Certification Exam
Question 1
A client would like to have a penetration test performed that leverages a continuously updated TTPs framework and covers a wide variety of enterprise systems and networks. Which of the following methodologies should be used to BEST meet the client's expectations?
- A. OWASP Top 10
- B. MITRE ATT&CK framework
- C. NIST Cybersecurity Framework
- D. The Diamond Model of Intrusion Analysis
Answer:
b
Question 2
Which of the following is the BEST resource for obtaining payloads against specific network infrastructure products?
- A. Exploit-DB
- B. Metasploit
- C. Shodan
- D. Retina
Answer:
a
Question 3
An exploit developer is coding a script that submits a very large number of small requests to a web server until the server is compromised. The script must examine each response received and compare the data to a large number of strings to determine which data to submit next. Which of the following data structures should the exploit developer use to make the string comparison and determination as efficient as possible?
- A. A list
- B. A tree
- C. A dictionary
- D. An array
Answer:
d
Question 4
A penetration tester ran a simple Python-based scanner. The following is a snippet of the code: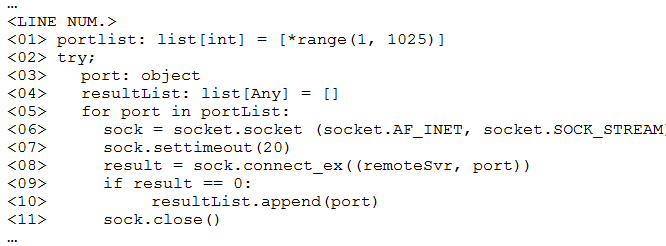
Which of the following BEST describes why this script triggered a `probable port scan` alert in the organization's IDS?
- A. sock.settimeout(20) on line 7 caused each next socket to be created every 20 milliseconds.
- B. *range(1, 1025) on line 1 populated the portList list in numerical order.
- C. Line 6 uses socket.SOCK_STREAM instead of socket.SOCK_DGRAM
- D. The remoteSvr variable has neither been type-hinted nor initialized.
Answer:
a
Question 5
A physical penetration tester needs to get inside an organization's office and collect sensitive information without acting suspiciously or being noticed by the security guards. The tester has observed that the company's ticket gate does not scan the badges, and employees leave their badges on the table while going to the restroom. Which of the following techniques can the tester use to gain physical access to the office? (Choose two.)
- A. Shoulder surfing
- B. Call spoofing
- C. Badge stealing
- D. Tailgating
- E. Dumpster diving
- F. Email phishing
Answer:
ad
Question 6
The attacking machine is on the same LAN segment as the target host during an internal penetration test. Which of the following commands will BEST enable the attacker to conduct host discovery and write the discovery to files without returning results of the attack machine?
- A. nmap -sn -n -exclude 10.1.1.15 10.1.1.0/24 -oA target_txt
- B. nmap -iR 10 -n -oX out.xml | grep "Nmap" | cut -d "" -f5 > live-hosts.txt
- C. nmap -Pn -sV -O -iL target.txt -oA target_text_Service
- D. nmap -sS -Pn -n -iL target.txt -oA target_txt1
Answer:
c
Question 7
A penetration tester is assessing a wireless network. Although monitoring the correct channel and SSID, the tester is unable to capture a handshake between the clients and the AP. Which of the following attacks is the MOST effective to allow the penetration tester to capture a handshake?
- A. Key reinstallation
- B. Deauthentication
- C. Evil twin
- D. Replay
Answer:
d
Question 8
A final penetration test report has been submitted to the board for review and accepted. The report has three findings rated high. Which of the following should be the NEXT step?
- A. Perform a new penetration test.
- B. Remediate the findings.
- C. Provide the list of common vulnerabilities and exposures.
- D. Broaden the scope of the penetration test.
Answer:
b
Question 9
A company has hired a penetration tester to deploy and set up a rogue access point on the network.
Which of the following is the BEST tool to use to accomplish this goal?
- A. Wireshark
- B. Aircrack-ng
- C. Kismet
- D. Wifite
Answer:
b
Reference:
https://null-byte.wonderhowto.com/how-to/hack-wi-fi-stealing-wi-fi-passwords-with-evil-twin-attack-0183880/
Question 10
PCI DSS requires which of the following as part of the penetration-testing process?
- A. The penetration tester must have cybersecurity certifications.
- B. The network must be segmented.
- C. Only externally facing systems should be tested.
- D. The assessment must be performed during non-working hours.
Answer:
c