comptia cs0-003 practice test
CompTIA CySA+ (CS0-003)
Question 1
A recent zero-day vulnerability is being actively exploited, requires no user interaction or privilege
escalation, and has a significant impact to confidentiality and integrity but not to availability. Which
of the following CVE metrics would be most accurate for this zero-day threat?
- A. CVSS: 31/AV: N/AC: L/PR: N/UI: N/S: U/C: H/1: K/A: L
- B. CVSS:31/AV:K/AC:L/PR:H/UI:R/S:C/C:H/I:H/A:L
- C. CVSS:31/AV:N/AC:L/PR:N/UI:H/S:U/C:L/I:N/A:H
- D. CVSS:31/AV:L/AC:L/PR:R/UI:R/S:U/C:H/I:L/A:H
Answer:
A
Explanation:
This answer matches the description of the zero-day threat. The attack vector is network (AV:N), the
attack complexity is low (AC:L), no privileges are required (PR:N), no user interaction is required
(UI:N), the scope is unchanged (S:U), the confidentiality and integrity impacts are high (C:H/I:H), and
the availability impact is low (A:L). Official Reference: https://nvd.nist.gov/vuln-metrics/cvss
Question 2
Which of the following tools would work best to prevent the exposure of PII outside of an
organization?
- A. PAM
- B. IDS
- C. PKI
- D. DLP
Answer:
D
Explanation:
Data loss prevention (DLP) is a tool that can prevent the exposure of PII outside of an organization by
monitoring, detecting, and blocking sensitive data in motion, in use, or at rest.
Question 3
An organization conducted a web application vulnerability assessment against the corporate website,
and the following output was observed: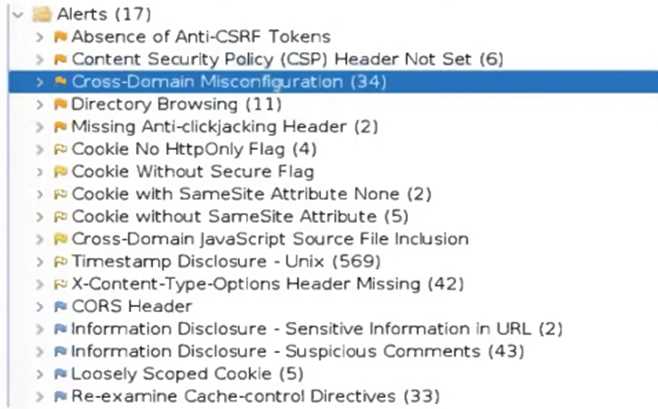
Which of the following tuning recommendations should the security analyst share?
- A. Set an HttpOnlvflaq to force communication by HTTPS
- B. Block requests without an X-Frame-Options header
- C. Configure an Access-Control-Allow-Origin header to authorized domains
- D. Disable the cross-origin resource sharing header
Answer:
B
Explanation:
The output shows that the web application is vulnerable to clickjacking attacks, which allow an
attacker to overlay a hidden frame on top of a legitimate page and trick users into clicking on
malicious links. Blocking requests without an X-Frame-Options header can prevent this attack by
instructing the browser to not display the page within a frame.
Question 4
Which of the following items should be included in a vulnerability scan report? (Choose two.)
- A. Lessons learned
- B. Service-level agreement
- C. Playbook
- D. Affected hosts
- E. Risk score
- F. Education plan
Answer:
D,E
Explanation:
A vulnerability scan report should include information about the affected hosts, such as their IP
addresses, hostnames, operating systems, and services. It should also include a risk score for each
vulnerability, which indicates the severity and potential impact of the vulnerability on the host and
the organization. Official Reference: https://www.first.org/cvss/
Question 5
The Chief Executive Officer of an organization recently heard that exploitation of new attacks in the
industry was happening approximately 45 days after a patch was released. Which of the following
would best protect this organization?
- A. A mean time to remediate of 30 days
- B. A mean time to detect of 45 days
- C. A mean time to respond of 15 days
- D. Third-party application testing
Answer:
A
Explanation:
A mean time to remediate (MTTR) is a metric that measures how long it takes to fix a vulnerability
after it is discovered. A MTTR of 30 days would best protect the organization from the new attacks
that are exploited 45 days after a patch is released, as it would ensure that the vulnerabilities are
fixed before they are exploited
Question 6
A security analyst recently joined the team and is trying to determine which scripting language is
being used in a production script to determine if it is malicious. Given the following script: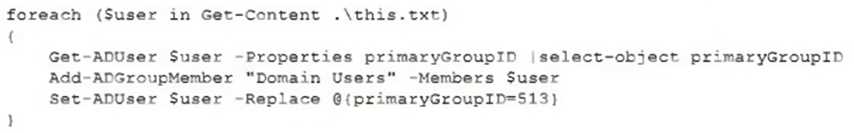
Which of the following scripting languages was used in the script?
- A. PowerShel
- B. Ruby
- C. Python
- D. Shell script
Answer:
A
Explanation:
The script uses PowerShell syntax, such as cmdlets, parameters, variables, and comments.
PowerShell is a scripting language that can be used to automate tasks and manage systems.
Question 7
A company's user accounts have been compromised. Users are also reporting that the company's
internal portal is sometimes only accessible through HTTP, other times; it is accessible through
HTTPS. Which of the following most likely describes the observed activity?
- A. There is an issue with the SSL certificate causinq port 443 to become unavailable for HTTPS access
- B. An on-path attack is being performed by someone with internal access that forces users into port
- C. The web server cannot handle an increasing amount of HTTPS requests so it forwards users to port
- D. An error was caused by BGP due to new rules applied over the company's internal routers
Answer:
B
Explanation:
An on-path attack is a type of man-in-the-middle attack where an attacker intercepts and modifies
network traffic between two parties. In this case, someone with internal access may be performing
an on-path attack by forcing users into port 80, which is used for HTTP communication, instead of
port 443, which is used for HTTPS communication. This would allow the attacker to compromise the
user accounts and access the company’s internal portal.
Question 8
A security analyst is tasked with prioritizing vulnerabilities for remediation. The relevant company
security policies are shown below:
Security Policy 1006: Vulnerability Management
1. The Company shall use the CVSSv3.1 Base Score Metrics (Exploitability and Impact) to prioritize
the remediation of security vulnerabilities.
2. In situations where a choice must be made between confidentiality and availability, the Company
shall prioritize confidentiality of data over availability of systems and data.
3. The Company shall prioritize patching of publicly available systems and services over patching of
internally available system.
According to the security policy, which of the following vulnerabilities should be the highest priority
to patch?
A)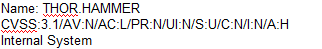
B)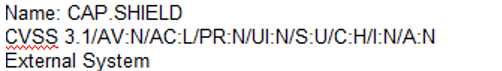
C)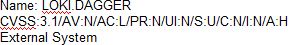
D)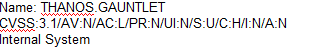
- A. Option A
- B. Option B
- C. Option C
- D. Option D
Answer:
C
Explanation:
According to the security policy, the company shall use the CVSSv3.1 Base Score Metrics to prioritize
the remediation of security vulnerabilities. Option C has the highest CVSSv3.1 Base Score of 9.8,
which indicates a critical severity level. The company shall also prioritize confidentiality of data over
availability of systems and data, and option C has a high impact on confidentiality (C:H). Finally, the
company shall prioritize patching of publicly available systems and services over patching of
internally available systems, and option C affects a public-facing web server. Official Reference:
https://www.first.org/cvss/
Question 9
Which of the following will most likely ensure that mission-critical services are available in the event
of an incident?
- A. Business continuity plan
- B. Vulnerability management plan
- C. Disaster recovery plan
- D. Asset management plan
Answer:
C
Question 10
The Chief Information Security Officer wants to eliminate and reduce shadow IT in the enterprise.
Several high-risk cloud applications are used that increase the risk to the organization. Which of the
following solutions will assist in reducing the risk?
- A. Deploy a CASB and enable policy enforcement
- B. Configure MFA with strict access
- C. Deploy an API gateway
- D. Enable SSO to the cloud applications
Answer:
A
Explanation:
A cloud access security broker (CASB) is a tool that can help reduce the risk of shadow IT in the
enterprise by providing visibility and control over cloud applications and services. A CASB can enable
policy enforcement by blocking unauthorized or risky cloud applications, enforcing data loss
prevention rules, encrypting sensitive data, and detecting anomalous user behavior.
Question 11
An incident response team receives an alert to start an investigation of an internet outage. The
outage is preventing all users in multiple locations from accessing external SaaS resources. The team
determines the organization was impacted by a DDoS attack. Which of the following logs should the
team review first?
- A. CDN
- B. Vulnerability scanner
- C. DNS
- D. Web server
Answer:
C
Explanation:
A distributed denial-of-service (DDoS) attack is a type of cyberattack that aims to overwhelm a
target’s network or server with a large volume of traffic from multiple sources. A common technique
for launching a DDoS attack is to compromise DNS servers, which are responsible for resolving
domain names into IP addresses. By flooding DNS servers with malicious requests, attackers can
disrupt the normal functioning of the internet and prevent users from accessing external SaaS
resources. Official Reference: https://www.eccouncil.org/cybersecurity-exchange/threat-
intelligence/cyber-kill-chain-seven-steps-cyberattack/
Question 12
A malicious actor has gained access to an internal network by means of social engineering. The actor
does not want to lose access in order to continue the attack. Which of the following best describes
the current stage of the Cyber Kill Chain that the threat actor is currently operating in?
- A. Weaponization
- B. Reconnaissance
- C. Delivery
- D. Exploitation
Answer:
D
Explanation:
The Cyber Kill Chain is a framework that describes the stages of a cyberattack from reconnaissance to
actions on objectives. The exploitation stage is where attackers take advantage of the vulnerabilities
they have discovered in previous stages to further infiltrate a target’s network and achieve their
objectives. In this case, the malicious actor has gained access to an internal network by means of
social engineering and does not want to lose access in order to continue the attack. This indicates
that the actor is in the exploitation stage of the Cyber Kill Chain. Official Reference:
https://www.lockheedmartin.com/en-us/capabilities/cyber/cyber-kill-chain.html
Question 13
An analyst finds that an IP address outside of the company network that is being used to run network
and vulnerability scans across external-facing assets. Which of the following steps of an attack
framework is the analyst witnessing?
- A. Exploitation
- B. Reconnaissance
- C. Command and control
- D. Actions on objectives
Answer:
B
Explanation:
Reconnaissance is the first stage in the Cyber Kill Chain and involves researching potential targets
before carrying out any penetration testing. The reconnaissance stage may include identifying
potential targets, finding their vulnerabilities, discovering which third parties are connected to them
(and what data they can access), and exploring existing entry points as well as finding new ones.
Reconnaissance can take place both online and offline. In this case, an analyst finds that an IP
address outside of the company network is being used to run network and vulnerability scans across
external-facing assets. This indicates that the analyst is witnessing reconnaissance activity by an
attacker. Official Reference: https://www.lockheedmartin.com/en-us/capabilities/cyber/cyber-kill-chain.html
Question 14
An incident response analyst notices multiple emails traversing the network that target only the
administrators of the company. The email contains a concealed URL that leads to an unknown
website in another country. Which of the following best describes what is happening? (Choose two.)
- A. Beaconinq
- B. Domain Name System hijacking
- C. Social engineering attack
- D. On-path attack
- E. Obfuscated links
- F. Address Resolution Protocol poisoning
Answer:
C,E
Explanation:
A social engineering attack is a type of cyberattack that relies on manipulating human psychology
rather than exploiting technical vulnerabilities. A social engineering attack may involve deceiving,
persuading, or coercing users into performing actions that benefit the attacker, such as clicking on
malicious links, divulging sensitive information, or granting access to restricted resources. An
obfuscated link is a link that has been disguised or altered to hide its true destination or purpose.
Obfuscated links are often used by attackers to trick users into visiting malicious websites or
downloading malware. In this case, an incident response analyst notices multiple emails traversing
the network that target only the administrators of the company. The email contains a concealed URL
that leads to an unknown website in another country. This indicates that the analyst is witnessing a
social engineering attack using obfuscated links.
Question 15
During security scanning, a security analyst regularly finds the same vulnerabilities in a critical
application. Which of the following recommendations would best mitigate this problem if applied
along the SDLC phase?
- A. Conduct regular red team exercises over the application in production
- B. Ensure that all implemented coding libraries are regularly checked
- C. Use application security scanning as part of the pipeline for the CI/CDflow
- D. Implement proper input validation for any data entry form
Answer:
C
Explanation:
Application security scanning is a process that involves testing and analyzing applications for security
vulnerabilities, such as injection flaws, broken authentication, cross-site scripting, and insecure
configuration. Application security scanning can help identify and fix security issues before they
become exploitable by attackers. Using application security scanning as part of the pipeline for the
continuous integration/continuous delivery (CI/CD) flow can help mitigate the problem of finding the
same vulnerabilities in a critical application during security scanning. This is because application
security scanning can be integrated into the development lifecycle and performed automatically and
frequently as part of the CI/CD process.