cisco 350-401 practice test
implementing cisco enterprise network core technologies (encor)
Question 1
Which DNS lookup does an access point perform when attempting CAPWAP discovery?
- A. CISCO-CONTROLLER.local
- B. CAPWAP-CONTROLLER.local
- C. CISCO-CAPWAP-CONTROLLER.local
- D. CISCO-DNA-CONTROLLER.local
Answer:
c
Reference:
http://www.revolutionwifi.net/revolutionwifi/2010/11/capwap-controller-discovery-process_23.html
Question 2
Please select the correct option that shows the correct combination for the Type 1 Hypervisor.
- A. Hardware; Hypervisor; Guest OS
- B. Hardware; Host OS; Hypervisor; Guest OS
- C. Host OS; Hypervisor; Guest OS
- D. Hardware; Host OS; Guest OS
Answer:
a
Question 3
Which Cisco DNA Center Assurance feature verifies host reachability?
- A. path trace
- B. application experience
- C. detail information
- D. network time travel
Answer:
a
Question 4
Refer to the exhibit.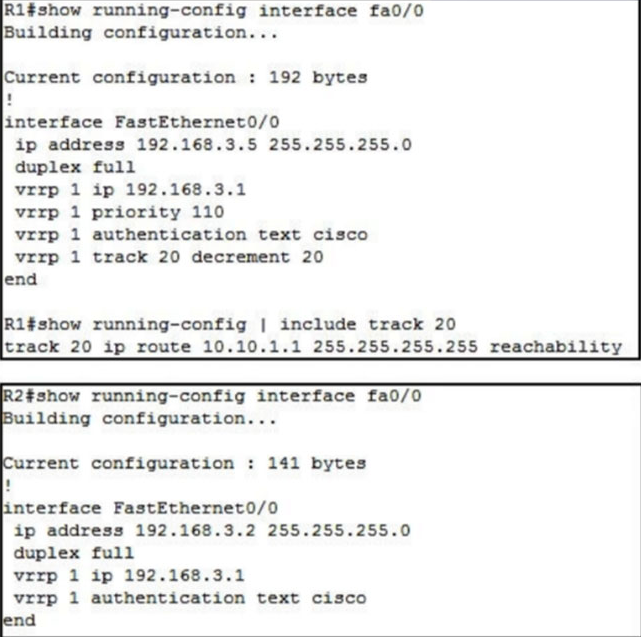
An engineer configures VRRP and issues the show commands to verify operation. What does the engineer confirm about VRRP group 1 from the output?
- A. Communication between VRRP members is encrypted using MD5.
- B. There is no route to 10.10.1.1/32 in R2's routing table.
- C. R1 is primary if 10.10.1.1/32 is in its routing table.
- D. If R1 reboots, R2 becomes the primary virtual router until R2 reboots.
Answer:
c
Question 5
DRAG DROP Drag and drop the QoS mechanisms from the left onto their descriptions on the right.
Select and Place: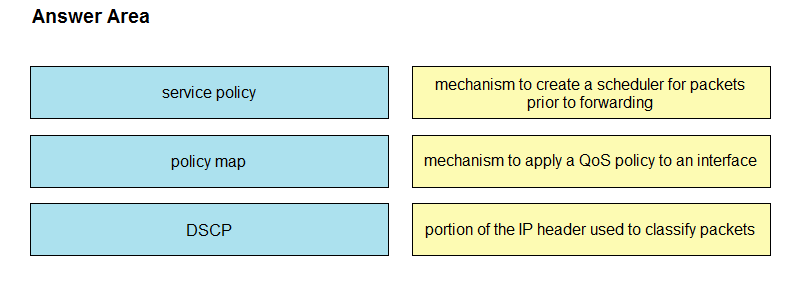
Answer:
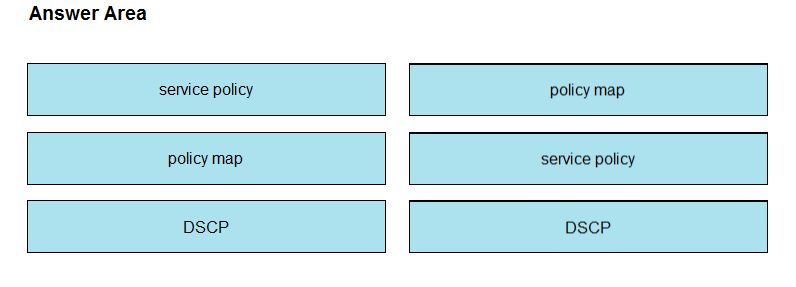
Question 6
What are two characteristics of Cisco SD-Access elements? (Choose two.)
- A. The border node is required for communication between fabric and nonfabric devices.
- B. Traffic within the fabric always goes through the control plane node.
- C. Fabric endpoints are connected directly to the border node.
- D. The control plane node has the full RLOC-to-EID mapping database.
- E. The border node has the full RLOC-to-EID mapping database.
Answer:
ad
Question 7
Which function is performed by vSmart in the Cisco SD-WAN architecture?
- A. aggregation and distribution of VPN routing information
- B. execution of localized policies
- C. facilitation of NAT detection and traversal
- D. redistribution between OMP and other routing protocols
Answer:
b
Question 8
Which method ensures the confidentiality of data exchanged over a REST API?
- A. Use the POST method instead of URL-encoded GET to pass parameters.
- B. Use TLS to secure the underlying HTTP session.
- C. Deploy digest-based authentication to protect the access to the API.
- D. Encode sensitive data using Base64 encoding.
Answer:
b
Question 9
Which activity requires access to Cisco DNA Center CLI?
- A. provisioning a wireless LAN controller
- B. creating a configuration template
- C. upgrading the Cisco DNA Center software
- D. graceful shutdown of Cisco DNA Center
Answer:
d
Question 10
What are two characteristics of VXLAN? (Choose two)
- A. It lacks support for host mobility.
- B. It uses VTEPs to encapsulate and decapsulate frames.
- C. It allows for up to 16 million VXLAN segments.
- D. It extends Layer 2 and Layer 3 overlay networks over a Layer 2 underlay.
- E. It has a 12-bit network identifier.
Answer:
bc