cisco 350-201 practice test
Performing CyberOps Using Core Security Technologies (CBRCOR)
Question 1
Refer to the exhibit.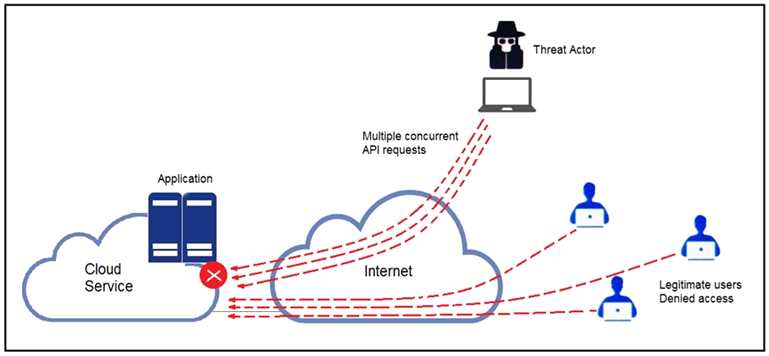
A threat actor behind a single computer exploited a cloud-based application by sending multiple
concurrent API requests. These requests made the application unresponsive. Which solution protects
the application from being overloaded and ensures more equitable application access across the
end-user community?
- A. Limit the number of API calls that a single client is allowed to make
- B. Add restrictions on the edge router on how often a single client can access the API
- C. Reduce the amount of data that can be fetched from the total pool of active clients that call the API
- D. Increase the application cache of the total pool of active clients that call the API
Answer:
A
Question 2
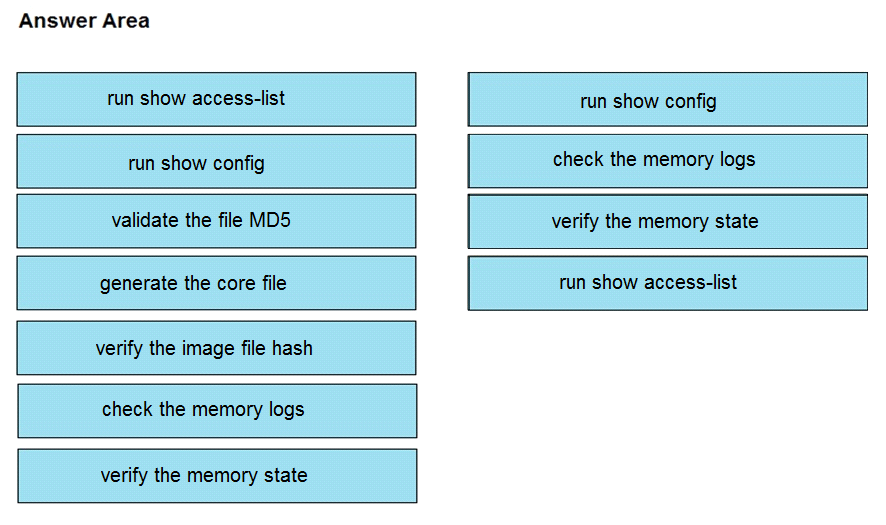
DRAG DROP
An organization lost connectivity to critical servers, and users cannot access business applications
and internal websites. An engineer checks the network devices to investigate the outage and
determines that all devices are functioning. Drag and drop the steps from the left into the sequence
on the right to continue investigating this issue. Not all options are used.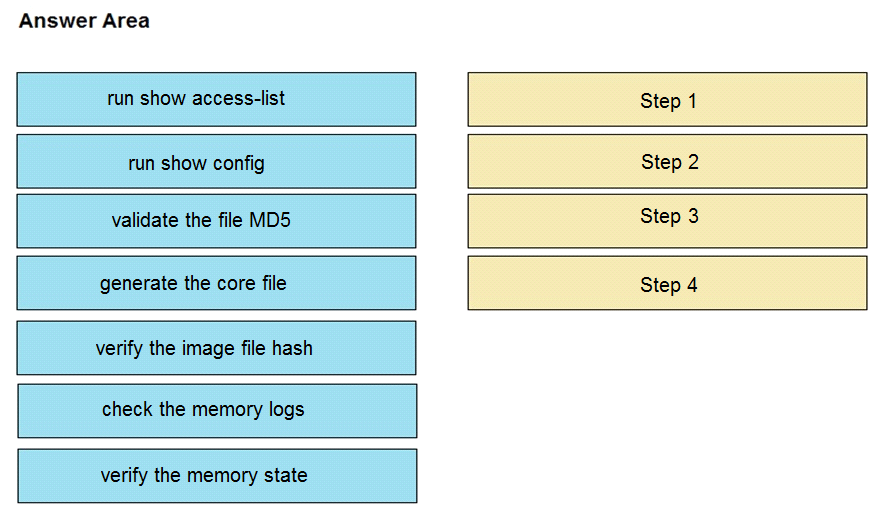
Answer:
Question 3
A threat actor attacked an organization’s Active Directory server from a remote location, and in a
thirty-minute timeframe, stole the password for the administrator account and attempted to access
3 company servers. The threat actor successfully accessed the first server that contained sales data,
but no files were downloaded. A second server was also accessed that contained marketing
information and 11 files were downloaded. When the threat actor accessed the third server that
contained corporate financial data, the session was disconnected, and the administrator’s account
was disabled. Which activity triggered the behavior analytics tool?
- A. accessing the Active Directory server
- B. accessing the server with financial data
- C. accessing multiple servers
- D. downloading more than 10 files
Answer:
C
Question 4
Refer to the exhibit.
A security analyst needs to investigate a security incident involving several suspicious connections
with a possible attacker. Which tool should the analyst use to identify the source IP of the offender?
- A. packet sniffer
- B. malware analysis
- C. SIEM
- D. firewall manager
Answer:
A
Question 5
Refer to the exhibit.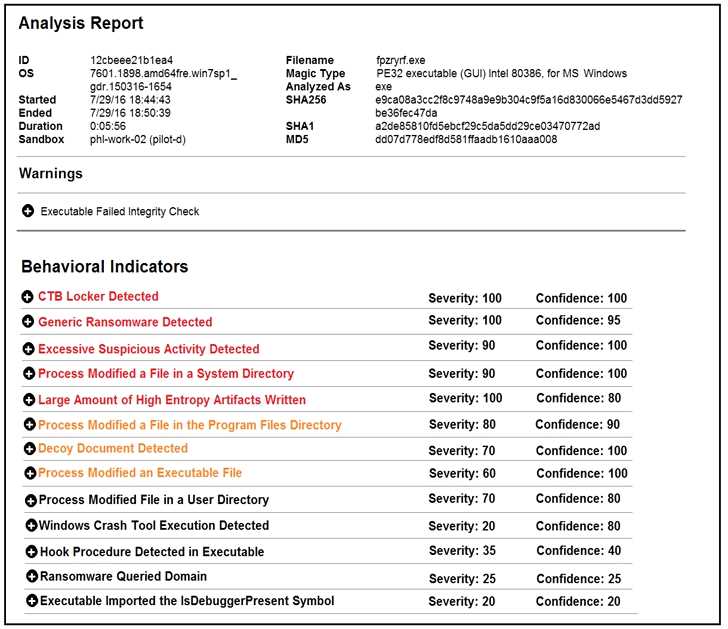
Cisco Advanced Malware Protection installed on an end-user desktop has automatically submitted a
low prevalence file to the Threat Grid analysis engine for further analysis. What should be concluded
from this report?
- A. The prioritized behavioral indicators of compromise do not justify the execution of the “ransomware” because the scores do not indicate the likelihood of malicious ransomware.
- B. The prioritized behavioral indicators of compromise do not justify the execution of the “ransomware” because the scores are high and do not indicate the likelihood of malicious ransomware.
- C. The prioritized behavioral indicators of compromise justify the execution of the “ransomware” because the scores are high and indicate the likelihood that malicious ransomware has been detected.
- D. The prioritized behavioral indicators of compromise justify the execution of the “ransomware” because the scores are low and indicate the likelihood that malicious ransomware has been detected.
Answer:
C
Question 6
The physical security department received a report that an unauthorized person followed an
authorized individual to enter a secured premise. The incident was documented and given to a
security specialist to analyze. Which step should be taken at this stage?
- A. Determine the assets to which the attacker has access
- B. Identify assets the attacker handled or acquired
- C. Change access controls to high risk assets in the enterprise
- D. Identify movement of the attacker in the enterprise
Answer:
D
Question 7
A new malware variant is discovered hidden in pirated software that is distributed on the Internet.
Executives have asked for an organizational risk assessment. The security officer is given a list of all
assets. According to NIST, which two elements are missing to calculate the risk assessment? (Choose
two.)
- A. incident response playbooks
- B. asset vulnerability assessment
- C. report of staff members with asset relations
- D. key assets and executives
- E. malware analysis report
Answer:
BE
Reference:
https://cloudogre.com/risk-assessment/
Question 8
Refer to the exhibit.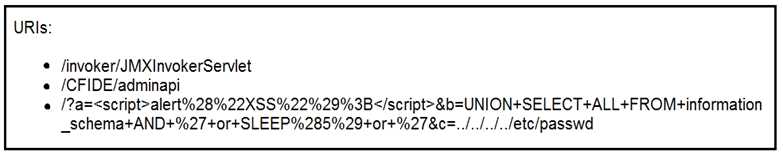
At which stage of the threat kill chain is an attacker, based on these URIs of inbound web requests
from known malicious Internet scanners?
- A. exploitation
- B. actions on objectives
- C. delivery
- D. reconnaissance
Answer:
C
Reference:
https://www2.deloitte.com/content/dam/Deloitte/sg/Documents/risk/sea-risk-cyber-
101-july2017.pdf
Question 9
Refer to the exhibit.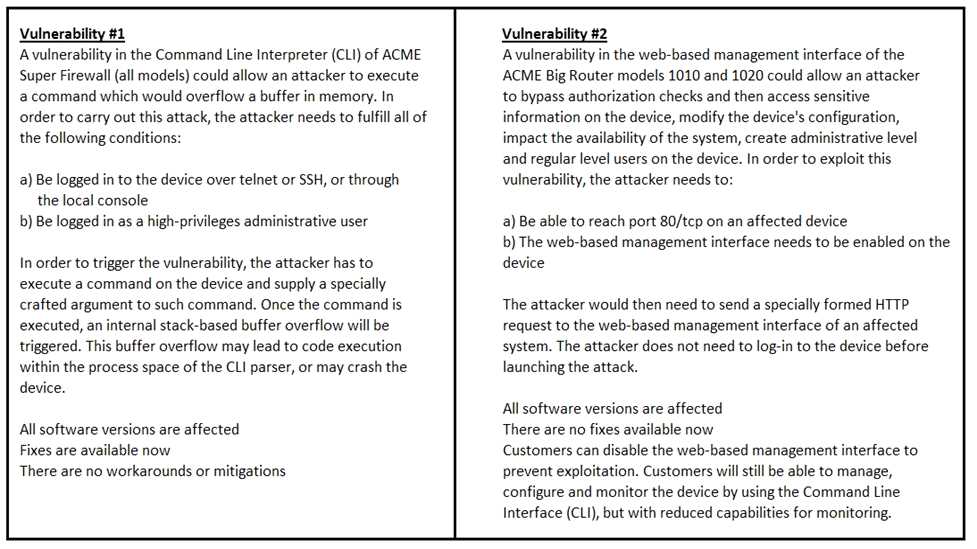
How must these advisories be prioritized for handling?
- A. The highest priority for handling depends on the type of institution deploying the devices
- B. Vulnerability #2 is the highest priority for every type of institution
- C. Vulnerability #1 and vulnerability #2 have the same priority
- D. Vulnerability #1 is the highest priority for every type of institution
Answer:
D
Question 10
Refer to the exhibit.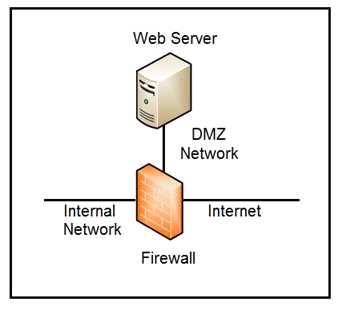
Which two steps mitigate attacks on the webserver from the Internet? (Choose two.)
- A. Create an ACL on the firewall to allow only TLS 1.3
- B. Implement a proxy server in the DMZ network
- C. Create an ACL on the firewall to allow only external connections
- D. Move the webserver to the internal network
Answer:
BD
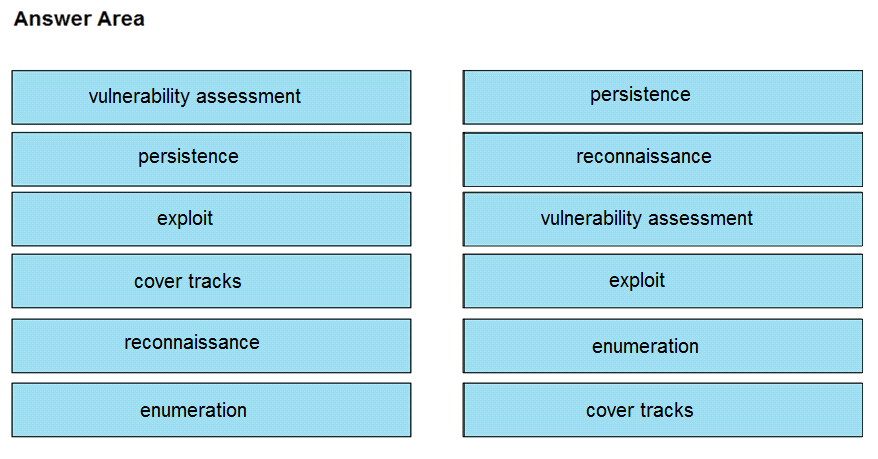
Question 11
DRAG DROP
Drag and drop the phases to evaluate the security posture of an asset from the left onto the activity
that happens during the phases on the right.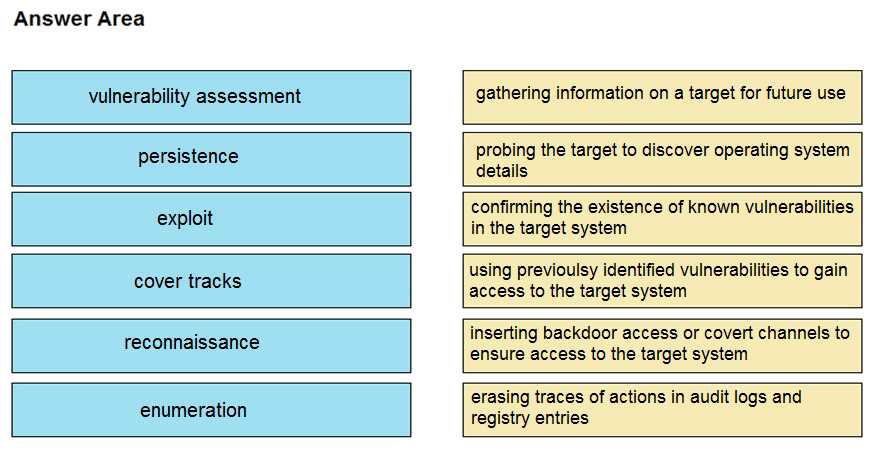
Answer:
Question 12
According to GDPR, what should be done with data to ensure its confidentiality, integrity, and
availability?
- A. Perform a vulnerability assessment
- B. Conduct a data protection impact assessment
- C. Conduct penetration testing
- D. Perform awareness testing
Answer:
B
Reference:
https://apdcat.gencat.cat/web/.content/03-documentacio/
Reglament_general_de_proteccio_de_dades/documents/DPIA-Guide.pdf
Question 13
A payroll administrator noticed unexpected changes within a piece of software and reported the
incident to the incident response team. Which actions should be taken at this step in the incident
response workflow?
- A. Classify the criticality of the information, research the attacker’s motives, and identify missing patches
- B. Determine the damage to the business, extract reports, and save evidence according to a chain of custody
- C. Classify the attack vector, understand the scope of the event, and identify the vulnerabilities being exploited
- D. Determine the attack surface, evaluate the risks involved, and communicate the incident according to the escalation plan
Answer:
B
Question 14
A company recently completed an internal audit and discovered that there is CSRF vulnerability in 20
of its hosted applications. Based on the audit, which recommendation should an engineer make for
patching?
- A. Identify the business applications running on the assets
- B. Update software to patch third-party software
- C. Validate CSRF by executing exploits within Metasploit
- D. Fix applications according to the risk scores
Answer:
D
Question 15
An engineer is analyzing a possible compromise that happened a week ago when the company ?
(Choose two.)
- A. firewall
- B. Wireshark
- C. autopsy
- D. SHA512
- E. IPS
Answer:
AB