cisco 300-725 practice test
securing the web with cisco web security appliance (300-725 swsa)
Question 1
Which certificate format does a Cisco WSA need when HTTPS proxy is configured?
- A. DER
- B. CER
- C. PEM
- D. CRL
Answer:
c
Reference:
https://community.cisco.com/t5/security-documents/wsa-training-series-how-to-configure-the-https-proxy-on-the/ta-p/3148673
Question 2
What is the primary benefit of using Cisco Advanced Web Security Reporting?
- A. ability to see the malicious activity of a user
- B. L4TM report with client-malware risk
- C. centralized and granular reporting
- D. access to a day report with historical data
Answer:
b
Reference:
https://www.cisco.com/c/en/us/products/collateral/security/web-security-appliance/datasheet_c78-729104.html
Question 3
How does dynamic content analysis improve URL categorization?
- A. It analyzes content based on cached destination content
- B. It adds intelligence to detect categories by analyzing responses
- C. It can be used as the only URL analysis method
- D. It analyzes content of categorized URL to tune decisions and correct categorization errors
Answer:
d
Reference:
https://www.cisco.com/c/en/us/support/docs/security/web-security-appliance/118063-qanda-wsa-00.html
Question 4
What is a benefit of integrating Cisco Cognitive Threat Analytics with a Cisco WSA?
- A. It adds additional information to the Cisco WSA reports
- B. It adds additional malware protection to the Cisco WSA
- C. It provides the ability to use artificial intelligence to block viruses
- D. It reduces time to identify threats in the network
Answer:
b
Reference:
https://www.ironportstore.com/datasheets/data_sheet_c78-729630.pdf
Question 5
When an access policy is created, what is the default option for the Application Settings?
- A. Use Global Policy Applications Settings
- B. Define the Applications Custom Setting
- C. Set all applications to Block
- D. Set all applications to Monitor
Answer:
b
Reference:
https://www.cisco.com/c/en/us/td/docs/security/wsa/wsa11-7/user_guide/b_WSA_UserGuide_11_7/b_WSA_UserGuide_11_7_chapter_01111.html
Question 6
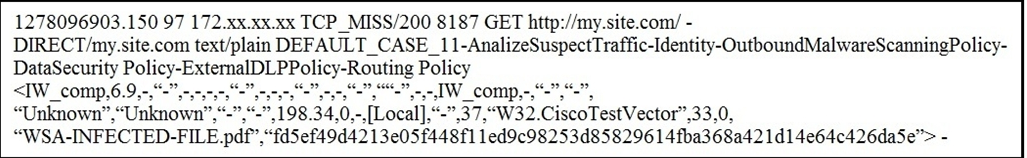
Refer to the exhibit. Which statement about the transaction log is true?
- A. The log does not have a date and time
- B. The proxy had the content and did not contact other servers
- C. The transaction used TCP destination port 8187
- D. The AnalizeSuspectTraffic policy group was applied to the transaction
Answer:
d
Question 7
Which method is used by AMP against zero-day and targeted file-based attacks?
- A. analyzing behavior of all files that are not yet known to the reputation service
- B. periodically evaluating emerging threats as new information becomes available
- C. implementing security group tags
- D. obtaining the reputation of known files
Answer:
d
Reference:
https://www.cisco.com/c/en/us/solutions/collateral/enterprise-networks/advanced-malware-protection/solution-overview-c22-734228.html
Question 8
What must be configured first when creating an access policy that matches the Active Directory group?
- A. authentication, authorization, and accounting of groups
- B. FQDN specification
- C. authentication realm
- D. authorized groups specification
Answer:
c
Reference:
https://www.cisco.com/c/en/us/support/docs/security/web-security-appliance/118005-configure-ntlm-00.html
Question 9
DRAG DROP Drag and drop the actions from the left into the correct order on the right in which they occur as an HTTPS session passes through the Cisco WSA.
Select and Place: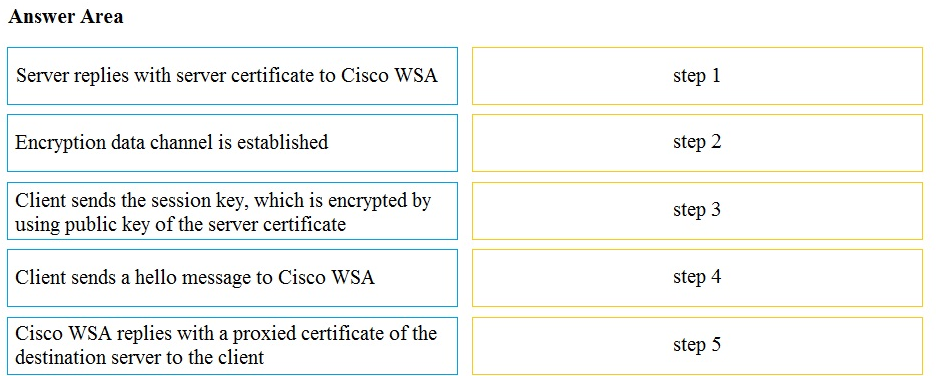
Answer:
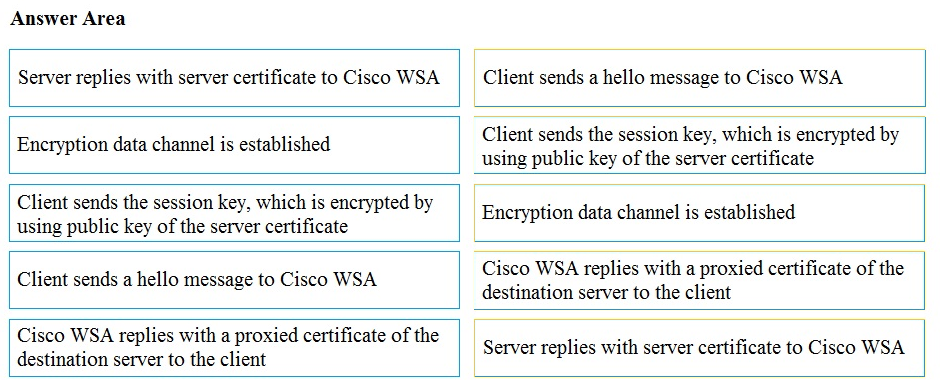
Question 10
An administrator wants to restrict file uploads to Facebook using the AVC feature.
Under which two actions must the administrator apply this restriction to an access policy? (Choose two.)
- A. Monitor Facebook General
- B. Monitor Social Networking
- C. Monitor Facebook Photos and Videos
- D. Monitor Facebook Messages and Chat
- E. Monitor Facebook Application
Answer:
ac
Reference:
https://www.cisco.com/c/en/us/products/collateral/security/web-security-appliance/datasheet-c78-741272.html