amazon AWS Certified SysOps Administrator (SOA-C01) practice test
Question 1
A user is planning to set up the Multi AZ feature of RDS. Which of the below mentioned conditions won't take advantage of
the Multi AZ feature?
- A. Availability zone outage
- B. A manual failover of the DB instance using Reboot with failover option
- C. Region outage
- D. When the user changes the DB instance’s server type
Answer:
C
Explanation:
Amazon RDS when enabled with Multi AZ will handle failovers automatically. Thus, the user can resume database
operations as quickly as possible without administrative intervention. The primary DB instance switches over automatically to
the standby replica if any of the following conditions occur:
An Availability Zone outage
The primary DB instance fails
The DB instance's server type is changed
The DB instance is undergoing software patching
A manual failover of the DB instance was initiated using Reboot with failover
Question 2
A user is using Cloudformation to launch an EC2 instance and then configure an application after the instance is launched.
The user wants the stack creation of ELB and AutoScaling to wait until the EC2 instance is launched and configured
properly. How can the user configure this?
- A. It is not possible that the stack creation will wait until one service is created and launched
- B. The user can use the HoldCondition resource to wait for the creation of the other dependent resources
- C. The user can use the DependentCondition resource to hold the creation of the other dependent resources
- D. The user can use the WaitCondition resource to hold the creation of the other dependent resources
Answer:
D
Explanation:
AWS Cloudformation is an application management tool which provides application modelling, deployment, configuration,
management and related activities. AWS CloudFormation provides a WaitCondition resource which acts as a barrier and
blocks the creation of other resources until a completion signal is received from an external source, such as a user
application or management system.
Question 3
You are attempting to connect to an instance in Amazon VPC without success. You have already verified that the VPC has
an Internet Gateway (IGW) the instance has an associated Elastic IP (EIP) and correct security group rules are in place.
Which VPC component should you evaluate next?
- A. The configuration of a NAT instance
- B. The configuration of the Routing Table
- C. The configuration of the internet Gateway (IGW)
- D. The configuration of SRC/DST checking
Answer:
B
Explanation:
Reference: http://docs.aws.amazon.com/ElasticLoadBalancing/latest/DeveloperGuide/UserScenariosForVPC.html
Question 4
You can create a CloudWatch alarm that watches a single metric. The alarm performs one or more actions based on the
value of the metric relative to a threshold over a number of time periods. Which of the following states is possible for the
CloudWatch alarm?
- A. OK
- B. ALERT
- C. THRESHOLD
- D. ERROR
Answer:
A
Explanation:
You can create a CloudWatch alarm that watches a single metric. The alarm performs one or more actions based on the
value of the metric relative to a threshold over a number of time periods. The action can be an Amazon EC2 action, an Auto
Scaling action, or a notification sent to an Amazon SNS topic.
An alarm has three possible states:
OK--The metric is within the defined threshold
ALARM--The metric is outside of the defined threshold
INSUFFICIENT_DATA--The alarm has just started, the metric is not available, or not enough data is available for the metric
to determine the alarm state Reference:
http://docs.aws.amazon.com/AmazonCloudWatch/latest/DeveloperGuide/AlarmThatSendsEmail.html
Question 5
An Administrator has an Amazon EC2 instance with an IPv6 address. The Administrator needs to prevent direct access to
this instance from the Internet.
The Administrator should place the EC2 instance in a:
- A. Private Subnet with an egress-only Internet Gateway attached to the subnet and placed in the subnet Route Table.
- B. Public subnet with an egress-only Internet Gateway attached to the VPC and placed in the VPC Route Table.
- C. Private subnet with an egress-only Internet Gateway attached to the VPC and placed in the subnet Route Table.
- D. Public subnet and a security group that blocks inbound IPv6 traffic attached to the interface.
Answer:
B
Question 6
A SysOps Administrator has been asked to configure user-defined cost allocation tags for a new AWS account. The
company is using AWS Organizations for account management.
What should the Administrator do to enable user-defined cost allocation tags?
- A. Log in to the AWS Billing and Cost Management console of the new account, and use the Cost Allocation Tags manager to create the new user-defined cost allocation tags.
- B. Log in to the AWS Billing and Cost Management console of the payer account, and use Cost Allocation Tags manager to create the new user-defined cost allocation tags.
- C. Log in to the AWS Management Console of the new account, use the Tag Editor to create the new user-defined tags, then use the Cost Allocation Tags manager in the new account to mark the tags as cost allocation tags.
- D. Log in to the AWS Management Console of the new account, use the Tag Editor to create the new user-defined tags, then use the Cost Allocation Tags manager in the payer account to mark the tags as cost allocation tags.
Answer:
B
Explanation:
Reference: https://docs.aws.amazon.com/awsaccountbilling/latest/aboutv2/activating-tags.html
Question 7
A block device is a storage device that moves data in sequences. How many types of block devices does Amazon EC2
support?
- A. 2 -instance store volumes and EBS volumes
- B. 5 -General Purpose SSD, Provisioned IOPS SSD, Throughput Optimized HDD, Cold HDD, and Magnetic
- C. 3 -SSD, HDD, and Magnetic
- D. 1 -instance store volumes
Answer:
A
Explanation:
A block device is a storage device that moves data in sequences of bytes or bits (blocks). These de-vices support random
access and generally use buffered I/O. Examples include hard disks, CD-ROM drives, and flash drives. A block device can
be physically attached to a computer or accessed remotely as if it were physically attached to the computer. Amazon EC2
supports two types of block devices: Amazon EC2 supports two types of block devices.
Instance store volumes (virtual devices whose underlying hardware is physically attached to the host computer for the
instance) EBS volumes (remote storage devices)
The SSD, HDD and Magnetic choices are all options for the type of storage offered via EBS vol-umes. They are not types of
block devices.
Reference:
http://docs.amazonwebservices.com/AWSEC2/latest/UserGuide/block-device-mapping-concepts.html
Question 8
A user has received a message from the support team that an issue occurred 1 week back between 3 AM to 4 AM and the
EC2 server was not reachable. The user is checking the CloudWatch metrics of that instance. How can the user find the data
easily using the CloudWatch console?
- A. The user can find the data by giving the exact values in the time Tab under CloudWatch metrics
- B. The user can find the data by filtering values of the last 1 week for a 1 hour period in the Relative tab under CloudWatch metrics
- C. It is not possible to find the exact time from the console. The user has to use CLI to provide the specific time
- D. The user can find the data by giving the exact values in the Absolute tab under CloudWatch metrics
Answer:
D
Explanation:
If the user is viewing the data inside the CloudWatch console, the console provides options to filter values either using the
relative period, such as days /hours or using the Absolute tab where the user can provide data with a specific date and time.
The console also provides the option to search using the local timezone under the time range caption in the console.
Question 9
An organization is measuring the latency of an application every minute and storing data inside a file in the JSON format.
The organization wants to send all latency data to AWS CloudWatch. How can the organization achieve this?
- A. The user has to parse the file before uploading data to CloudWatch
- B. It is not possible to upload the custom data to CloudWatch
- C. The user can supply the file as an input to the CloudWatch command
- D. The user can use the CloudWatch Import command to import data from the file to CloudWatch
Answer:
C
Explanation:
AWS CloudWatch supports the custom metrics. The user can always capture the custom data and upload the data to
CloudWatch using CLI or APIs. The user always has to include the namespace as part of the request. If the user wants to
upload the custom data from a file, he can supply file name along with the parameter -- metric-data to command put-metric-
data.
Question 10
What is a "vault" in Amazon Glacier?
- A. A unique ID that maps an AWS Region, plus a specific Amazon S3 bucket
- B. A way to group archives together in Amazon Glacier
- C. A container for storing S3 buckets
- D. A free tier available for 12 months following your AWS sign-up date
Answer:
B
Explanation:
An Amazon Glacier vault is a container in which you can organize and manage your archives.
You store data in Amazon Glacier as an archive. Each archive is assigned a unique archive ID that can later be used to
retrieve the data. An archive can represent a single file or you may choose to combine several files to be uploaded as a
single archive. You upload archives into vaults. Vaults are collections of archives that you use to organize your data.
Reference: http://aws.amazon.com/glacier/faqs/#How_do_vaults_work
Question 11
A user is measuring the CPU utilization of a private data center machine every minute. The machine provides the aggregate
of data every hour, such as Sum of data, Min value, Max value, and Number of Data points.
The user wants to send these values to CloudWatch. How can the user achieve this?
- A. Send the data using the put-metric-data command with the aggregate-values parameter
- B. Send the data using the put-metric-data command with the average-values parameter
- C. Send the data using the put-metric-data command with the statistic-values parameter
- D. Send the data using the put-metric-data command with the aggregate –data parameter
Answer:
C
Explanation:
AWS CloudWatch supports the custom metrics. The user can always capture the custom data and upload the data to
CloudWatch using CLI or APIs. The user can publish the data to CloudWatch as single data points or as an aggregated set
of data points called a statistic set using the command put-metric-data. When sending the aggregate data, the user needs to
send it with the parameter statistic-values: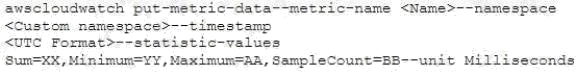
Question 12
A SysOps Administrator has an AWS CloudFormation template of the companys existing infrastructure in us-west-2. The
Administrator attempts to use the template to launch a new stack in eu-west-1, but the stack only partially deploys, receives
an error message, and then rolls back.
Why would this template fail to deploy? (Choose two.)
- A. The template referenced an IAM user that is not available in eu-west-1
- B. The template referenced an Amazon Machine Image (AMI) that is not available in eu-west-1
- C. The template did not have the proper level of permissions to deploy the resources
- D. The template requested services that do not exist in eu-west-1
- E. CloudFormation templates can be used only to update existing services
Answer:
B C
Question 13
A company is using an AWS KMS customer master key (CMK) with imported key material. The company references the
CMK by its alias in the Java application to encrypt data. The CMK must be rotated every 6 months.
What is the process to rotate the key?
- A. Enable automatic key rotation for the CMK, and specify a period of 6 months.
- B. Create a new CMK with new imported material, and update the key alias to point to the new CMK.
- C. Delete the current key material, and import new material into the existing CMK.
- D. Import a copy of the existing key material into a new CMK as a backup, and set the rotation schedule for 6 months.
Answer:
A
Explanation:
Cryptographic best practices discourage extensive reuse of encryption keys. To create new cryptographic material for your
AWS Key Management Service (AWS KMS) customer master keys (CMKs), you can create new CMKs, and then change
your applications or aliases to use the new CMKs. Or, you can enable automatic key rotation for an existing CMK.
When you enable automatic key rotation for a customer managed CMK, AWS KMS generates new cryptographic material for
the CMK every year. AWS KMS also saves the CMK's older cryptographic material in perpetuity so it can be used to decrypt
data that it encrypted. AWS KMS does not delete any rotated key material until you delete the CMK. Reference:
https://docs.aws.amazon.com/kms/latest/developerguide/rotate-keys.html
Question 14
An enterprise is using federated Security Assertion Markup Language (SAML) to access the AWS Management Console.
How should the SAML assertion mapping be configured?
- A. Map the group attribute to an AWS group. The AWS group is assigned IAM policies that govern access to AWS resources.
- B. Map the policy attribute to IAM policies the federated user is assigned to. These policies govern access to AWS resources.
- C. Map the role attribute to an AWS role. The AWS role is assigned IAM policies that govern access to AWS resources.
- D. Map the user attribute to an AWS user. The AWS user is assigned specific IAM policies that govern access to AWS resources.
Answer:
C
Explanation:
Reference: https://docs.aws.amazon.com/IAM/latest/UserGuide/id_roles_providers_create_saml_assertions.html
Question 15
A database is running on an Amazon RDS Multi-AZ DB instance. A recent security audit found the database to be out of
compliance because it was not encrypted.
Which approach will resolve the encryption requirement?
- A. Log in to the RDS console and select the encryption box to encrypt the database.
- B. Create a new encrypted Amazon EBS volume and attach it to the instance.
- C. Encrypt the standby replica in the secondary Availability Zone and promote it to the primary instance.
- D. Take a snapshot of the RDS instance, copy and encrypt the snapshot, and then restore to the new RDS instance.
Answer:
A